Steering Through a Breach: JLR’s Wake-Up Call for Manufacturers Everywhere
JLR Cyberattack: What Happened, Why It Matters, and What Leaders Should Do Next
Who : Jaguar Land Rover (JLR) the UK’s largest automaker and a wholly-owned subsidiary of Tata Motors reported £29.0B FY25 revenue and 10 consecutive profitable quarters before this incident. Headcount sits in the 32–35K employees range (UK and global), with a supply chain touching ~200K jobs.
What happened : A cyber incident detected Aug 31–Sep 2, 2025 forced JLR to pause production and retail operations while shutting down systems to contain impact. As of Sep 23–24, JLR extended the production pause to Oct 1 while planning a phased restart. The UK government is coordinating with industry on supplier relief.
Impact : The outage has stalled factories for several weeks, straining the automotive supply chain and cashflows for hundreds of suppliers. Multiple outlets estimate weekly losses and highlight that JLR lacks cyber-insurance coverage, bearing the full cost of the disruption.
How it happened : JLR has not publicly confirmed root cause. Third-party research suggests a ransomware-style intrusion potentially leveraging stolen Jira credentials, followed by PowerShell-based persistence, AMSI bypasses, reflective loading, and Sliver C2 tactics consistent with modern post-exploitation tradecraft. Treat this as informed but unconfirmed attribution pending JLR’s forensics.
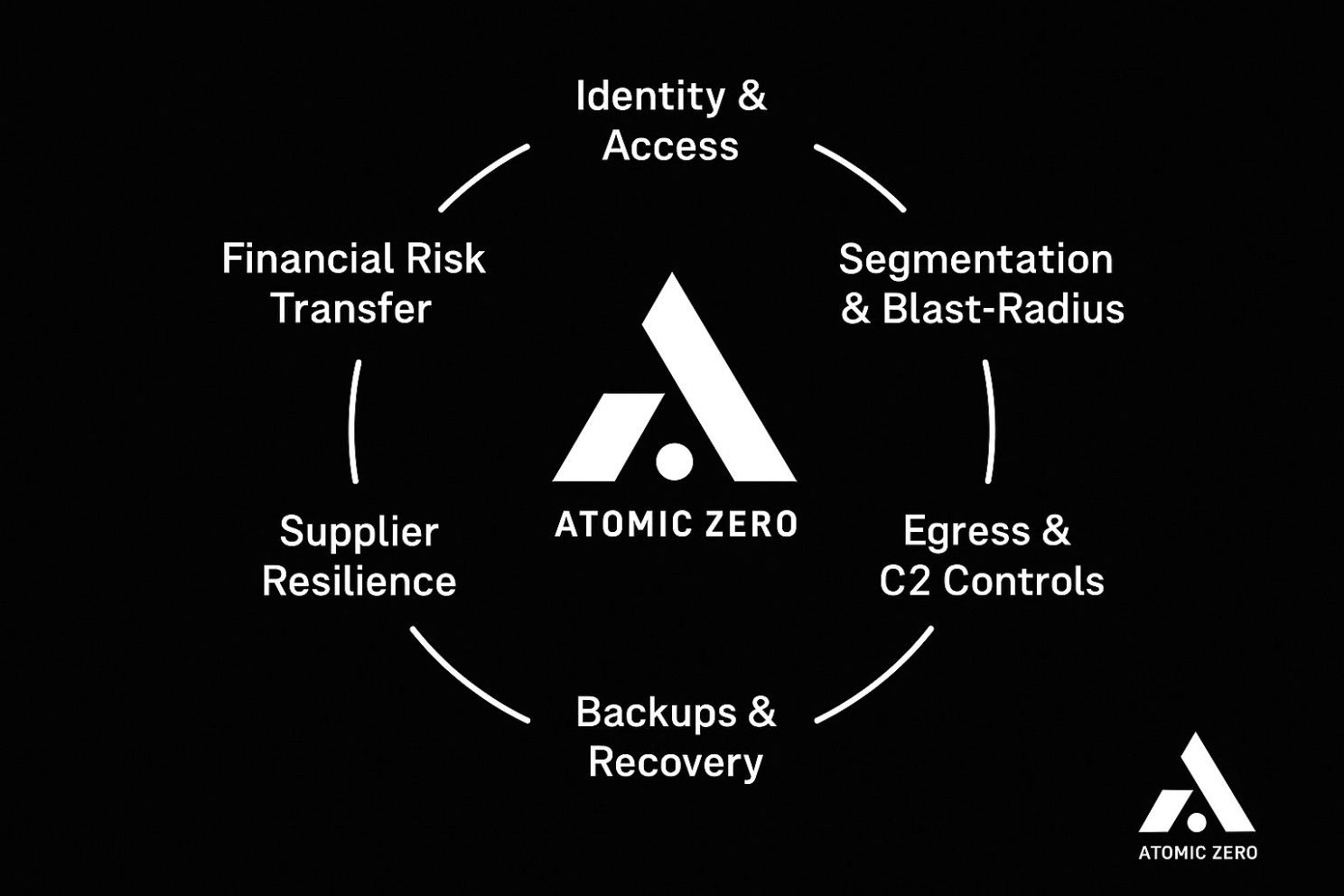
CISO & C-Suite Take Away
Lessons for CISOs & the C-suite
Identity & Access: Assume credential theft. Enforce phishing-resistant MFA, conditional access, device trust, and Just-In-Time/Just-Enough-Access for both workforce and third-party accounts.
Segmentation & Blast-Radius: Separate IT/OT domains; enforce service isolation, brokered access, and default-deny east-west policies so plant operations don’t fall with enterprise IT.
Egress & C2 Controls: Stop Sliver/“living off the land” traffic with egress allow-lists, TLS inspection where lawful, command-line auditing, and AMSI eventing.
Backups & Recovery: Immutable, offline, frequently tested. Measure RTO/RPO realism via periodic plant-level exercises.
Supplier Resilience: Pre-agree emergency payment rails and inventory buffers; require SBOMs, incident notification SLAs, and credential hygiene from critical vendors.
Financial Risk Transfer: Calibrate cyber-insurance to operational risk; model plant downtime and supplier failure scenarios explicitly many firms discover policy gaps during claims. (Recent reporting indicates no cyber-insurance here, magnifying losses.)
Post-breach actions JLR-style manufacturers should take next
Contain & Verify: Flatten persistence (script block logging, AMSI, EDR memory scans); rotate all privileged & third-party creds; re-image gold builds.
Phased Restart Guardrails: Bring back identity, logging, and egress controls first, then core ERP/MES, then plant OT each with tripwires (SOAR playbooks + SIEM rules) before moving to the next phase.
Supplier Lifelines: Fast-track manual/AP emergency payments, provide secure portals with short-lived credentials, and communicate restart windows to reduce insolvency risk in the tiered supply base.
Regulatory & Stakeholder Comms: Maintain transparent, timestamped status updates; coordinate with government where national supply chains are affected. (The UK government has publicly acknowledged the supply-chain impact.)
Why this matters This isn’t just another IT incident - it’s a manufacturing continuity crisis. The delta between “IT lock-down” and “safe, staged OT restart” is where economic damage explodes. Leaders should measure readiness in days of production saved, not just mean-time metrics.
Tools that help (categories)
Identity & Privilege: phishing-resistant MFA, PAM/JIT (e.g., strong PAM + device trust)
EDR/XDR + Memory Forensics: detect reflective loaders and Sliver C2 patterns
Network/Egress Controls: zero-trust gateways, DNS/HTTP egress allow-lists, OT-aware firewalls
SIEM + SOAR: prebuilt detections for AMSI bypasses/PowerShell abuse; automated containment
Backup/Recovery: immutable, isolated stores with plant-level rehearse-and-recover drills
SBOM/Third-party Risk: continuous posture checks on suppliers (credentials, patch SLAs)
If you would like to have a need for advisory or technical dialogue about this breach or needing help in solving security problems, feel free to reach out.
