What can you do in preparation for downstream attacks after credential harvesting?
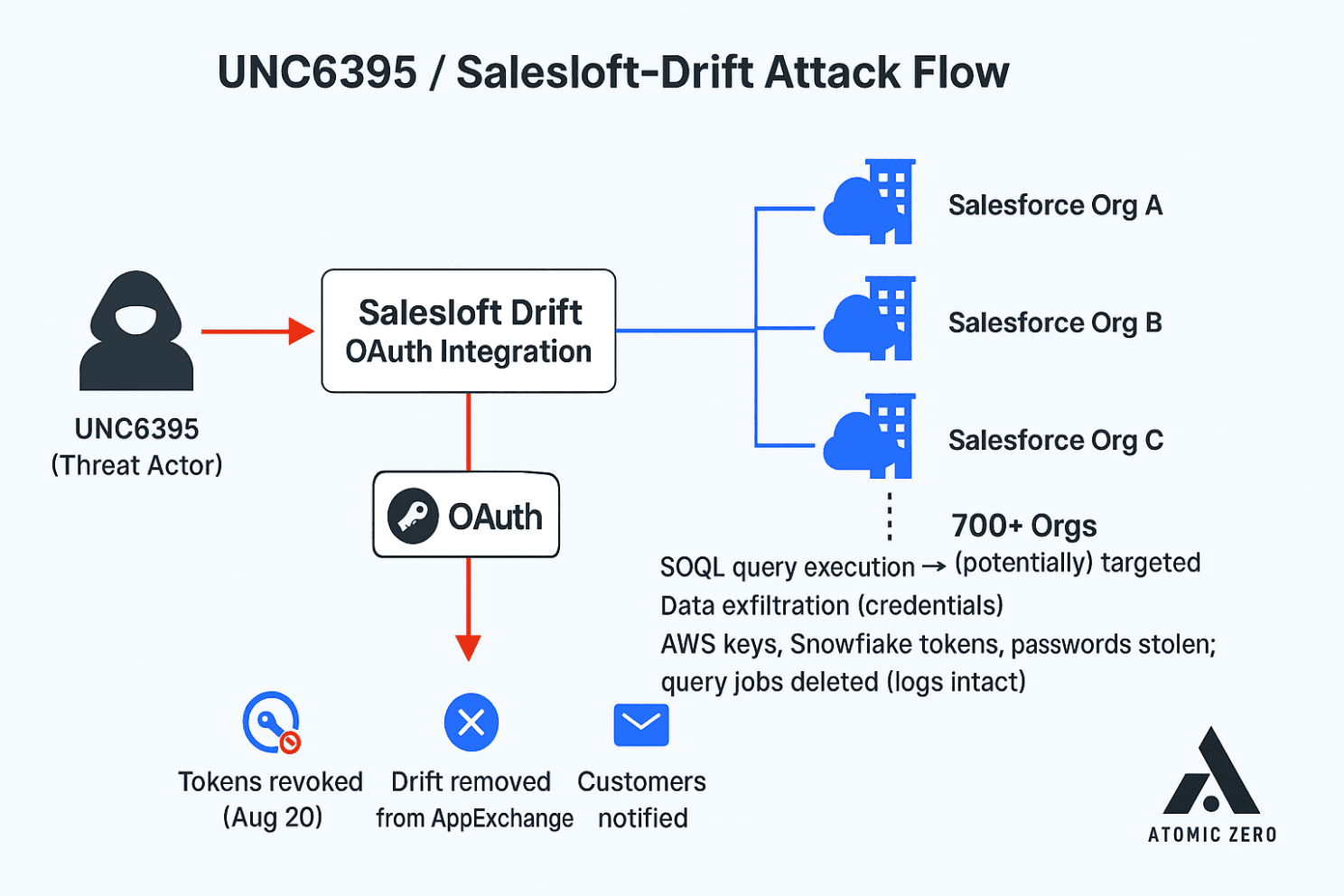
Now that GTIG and other formidable researchers in many entities have confirmed 100's of organizations are potentially impacted. Let's dive into what is recommended you do next as credential harvesting in SaaS/SaaS-to-SaaS integrations (like the UNC6395/040/ Drift attack) is particularly dangerous because it enables downstream attacks: once attackers obtain cloud/API credentials, they pivot into other systems (AWS, Snowflake, internal apps, etc.).
A Structured breakdown of recommendation on downstream attacks, feel free to add any more on comments after all Cyber Security is a team sport.
🔑 1. Harden Credential Management
Short-lived tokens & keys: Replace long-lived OAuth tokens and static API keys with short-lived, automatically rotated credentials.
Enforce expiration & rotation: All secrets should auto-expire and rotate regularly (hours/days, not months).
Scope credentials tightly: Use least privilege tokens should only access the specific objects/functions needed.
🔍 2. Monitor & Detect Anomalies
Behavioral monitoring: Flag when a token is suddenly used in new geographies, unusual volume of API calls, or accessing new data objects.
Downstream visibility: Log when Salesforce (or any SaaS) queries contain secrets (e.g., AWS keys stored in Notes/Custom Objects).
Job deletion alerts: If queries/jobs are being deleted systematically, raise red flags attackers often use this for stealth.
🛡️ 3. Secure Non-Human Identities
Inventory SaaS-to-SaaS connections: Know every app that connects via OAuth to Salesforce, Google Workspace, etc.
Revoke unused integrations: Periodically audit and disable stale/unused OAuth tokens and app connections.
Identity segmentation: Treat integrations as “non-human identities” and govern them with the same rigor as admin accounts.
🚨 4. Contain & Limit Blast Radius
Token binding: Bind tokens to specific device/app contexts to prevent replay from rogue environments.
Network controls: Enforce conditional access block API calls from Tor/VPNs or geographies irrelevant to your org.
Data segregation: Don’t store high-value secrets (like AWS keys or DB creds) inside SaaS objects. If credentials must be stored, vault them and tokenize them.
🧪 5. Test & Drill
Red team simulations: Test harvesting and replay scenarios from SaaS apps → downstream systems.
Incident response playbooks: Have a runbook for revoking OAuth tokens at scale (like Salesforce did with Drift).
Tabletop exercises: Run “what if Salesforce credential harvesting occurs” across your SecOps + IT + IAM teams.
✅ 6. Vendor Risk Governance
Third-party due diligence: Assess SaaS vendors for their OAuth handling, credential storage, and monitoring practices.
Contractual controls: Require vendors to notify you of token theft or breaches rapidly.
Zero-trust approach: Don’t assume vendor integrations are safe, enforce conditional access and monitoring even on “trusted” apps.
📌 Bottom Line
Downstream attacks happen because one credential = access everywhere. The key defenses are: rotate quickly, scope tightly, monitor aggressively, and vault wisely.
